Welcome back to the Geneva Dialogue! Since 2018, this international process has been focusing on responsible behavior in cyberspace and exploring ways to enhance cyber stability. Over the years, we’ve built a community with partners from diverse industries and who are leading in digitisation, including the manufacturing of digital products.
This year, the Geneva Dialogue is going to the next level. Led by the Swiss Federal Department of Foreign Affairs (FDFA) and implemented by Diplo with the support of C4DT, the Dialogue will focus on the implementation of cyber norms related to reducing vulnerabilities in digital products and supply chain security. In particular, we’re delving into the roles and responsibilities of various non-state actors.
To investigate the topic, the Dialogue recently held a two-part webinar through a public conversation format. As eloquently framed by Nina Katharina Frey (Swiss Foreign Ministry of Federal Affairs, FDFA), the Geneva Dialogue aims to enhance good practices and identify good practices to ensure the implementation of cyber norms and principles.

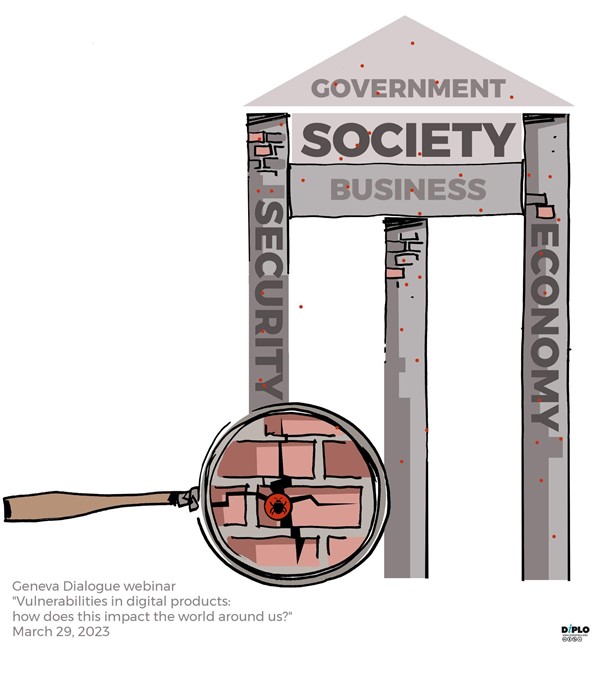
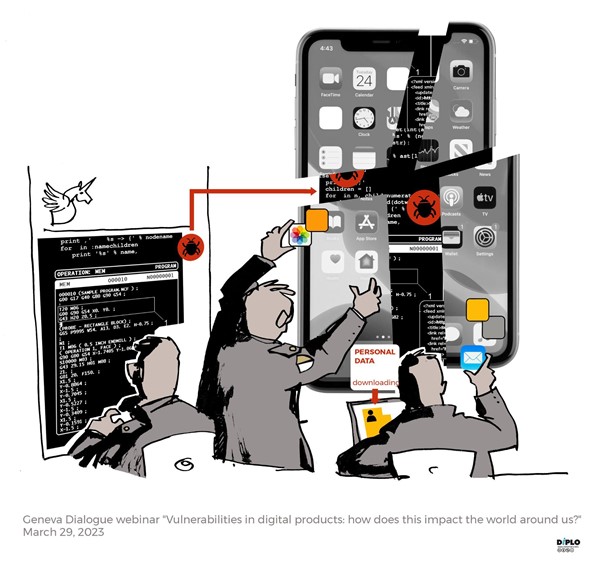
The first webinar (held on 29 March) focused on three stories – SolarWinds hack, the use of Pegasus spyware, and Colonial Pipeline ransomware attack. They all have different targets, threat actors, and impact, but somehow the same origin – exploiting a software vulnerability. The moderator, Maya Bundt (Swiss Risk Association), asked what they had in common? What role do software vulnerabilities play in human society’s vulnerabilities today? What dangers vulnerable digital products create for different stakeholders and communities? And, most importantly, whose responsibility is it to fix all this?
Ivan Kwiatkowski (Kaspersky) started with the SolarWinds case, and stressed that vulnerabilities affect both the user and the software vendors, and thus concern the security of everyone. Therefore, we must always assume that we, as users, have been compromised, and start looking at traces rather than relying on just having a secure network.
From a human rights perspective, Natalia Krapiva (AccessNow) spoke about the Pegasus case and the impact of spyware exploiting vulnerabilities. This spyware was used to target journalists and activists and resulted in human rights abuses including but not limited to the right to privacy, freedom of expression, and right to a fair trial. It is thus imperative that urgent action is taken, as attacks with the use of spyware continue to target civil society.
Another sector in which vulnerabilities have displayed their impact is critical infrastructure. Steven Sim (OT-ISAC) spoke about the Colonial Pipeline ransomware incident which disrupted the supply chain for essential fuel. The attack affected consumers and airlines in the USA, resulting in a shortage of gasoline, jet fuel, and home heating oil, leading the US government to declare a state of emergency. It was found that the attackers relied on a reused employee’s VPN password that did not have multi-factor authentication. Steven stated that the attackers in the incident exploited vulnerabilities not just across the technology, but people and processes, as well. Therefore, to overcome and combat this issue, it is important to enhance the public-private relationship where government and regulators will take action.

It is thus seen that the vulnerabilities can affect anyone in any sector and produce diverse effects for societies. Who is expected to take primary action to minimise the risks? What are the roles and responsibilities of manufacturers of digital products? Or Governments, and users?
We zoomed into these subtopics at the second part on 4 April, moderated by Vladimir Radunović (DiploFoundation).

Four experts represented different stakeholder groups and perspectives – industry manufacturer, former government and diplomat, open source expert and independent software developer, and global consumer perspective. Sofia Martinez-Gomez (Roche Diagnostics) started with outlining key challenges from a healthcare perspective. She emphasized that the outmost priority of cybersecurity in the healthcare sector is protecting people’s lives and ensuring their safety. Data confidentiality and protecting user privacy when using medical devices is another goal for her organization. Although digitalisation brings benefits to the healthcare industry, it also introduces new challenges, such as supply chain risks and fragmented ownership of product security. To address these challenges, regulators set requirements and guiding principles, and companies have a responsibility to provide security by design and default practices. However, securing digital products throughout their lifecycle requires collaboration between different stakeholders.
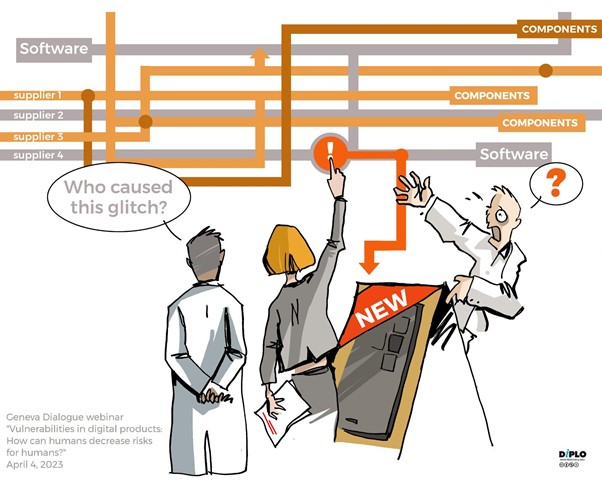
Bert Hubert (independent entrepreneur and software developer) reiterated the lack of transparency within companies about what is included in their products, and stressed that this makes protecting and supporting such products very difficult. Open source software is often used without compliance departments knowing about it. It is free and doesn’t require contracts to be signed. However this can lead to questionable reliance and unsupported dependencies.

Do governments have a responsibility? Katherine Getao (Cyber Hygiene, Cyber Diplomacy, and ICT Strategy and Governance Consultant) stressed that yes – they are responsible for protecting citizens and enforcing responsible behaviour in the technology space. She identified three types of vulnerabilities in technology: by definition, by design, and by deficiency, and added that governments need to step in and create proper environments to deal with these vulnerabilities. Kathrine also emphasised the importance of capacity building for both the developers and the users, and that products sold to African governments and developing countries should not be deficient by design or by deficiency.
Javier Ruiz Diaz (Consumers International), representing the consumer perspective, added that companies and regulators have a role to play in ensuring product safety, but that consumers should not be solely responsible for their security. Education, labelling, and setting safety standards, is essential in order to ensure product safety. Javier also emphasised the importance of understanding the economics of cybersecurity. That includes understanding who will pay for the costs, who will be liable, and how to distribute the costs among the stakeholders. This is an area where governments may have a role to play, while it is important to understand how to distribute liabilities.

So, what is the solution? Just as a Facebook status says, ‘it’s complicated’. But that doesn’t mean that we shouldn’t explore these complexities further. And, that’s exactly what the 2023 edition of the Geneva Dialogue aims to do: bring people together, listen to each other, and learn from different perspectives on how to find solutions that may benefit us all. Stay tuned!